Cloud computing security is an integral part of information security in cloud computing. Security is one of the most important concerns for information technology companies today. The need for information security in cloud computing is evident from the constantly increasing amount of data being stored by businesses. And with an estimated 4.2 billion gigabytes of data expected to be stored within the cloud by the year 2021, there is no doubt that there will be a large demand for cloud security solutions.
Types Of Safety Management Systems:

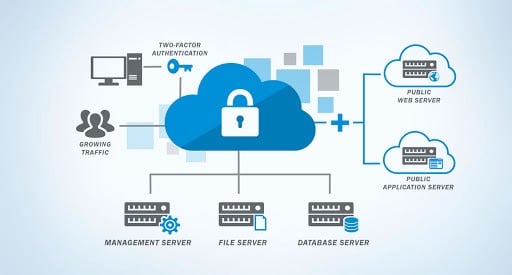
When it comes to cloud computing security, there are two types of safety management systems: managed and self-service. Managed security providers (MSPs) are those organizations that provide cloud computing security services based on traditional ITIL processes. Self-service security providers (SSPs) are those provided by the cloud environment. The two types of management systems have different requirements for application deployment. However, both also share some common controls that allow for data security throughout the entire network.
Management of data is the most important benefit of using cloud resources. The most important aspect of a cloud security system is its capability to provide application security. The security system must be robust enough to ensure that data is secured even when it is not in use by end-users. An effective cloud security system must be able to restrict the access of third parties to data that are in the user’s local area. In addition to restricting access, the security system must also restrict access of servers to unauthorized users. Some of the benefits of a robust security system include preventing attacks, detecting and blocking intrusions, and protecting data from an unauthorized transfer.
Major Concern:
Security issues are usually a major concern for information technology companies. The biggest issues for many of these companies involve data centers, which are among the most important parts of a cloud computing arrangement. Many businesses are now moving their IT operations to data centers that are located within the enterprise. This provides them with better flexibility, but it comes with more responsibilities as well. One of the most critical issues in information security, especially in cases where business information passes through these centers.
Information that passes through a data center can be compromised when it is in the hands of unprofessional personnel. The same can be said about the infrastructure, particularly the servers. Cloud computing solutions rely on a strong infrastructure to provide fast and reliable performance. These solutions ensure that the servers used by the cloud environment do not become a target for attack. They also use highly efficient firewall systems to prevent intrusion attempts and hackers, ensuring data confidentiality.
In cases where the organization is not able to provide its own IT infrastructure, cloud service providers often provide security services. In fact, some of these service providers offer fully managed and maintained public cloud facilities. These include security, monitoring, upgrades, patches, application updates, and more. The cost of such services depends on the degree of security, the organization requires and the bandwidth availability of the public cloud environment.
Open Source Technology:
With the advent of open source technologies and virtualization, security requirements for cloud applications have gone far beyond what they were at any point in the past. Today’s modern VDI and iaaS models allow for a tremendous degree of flexibility. They enable every application to run on its own virtual infrastructure without relying on a single physical server. Some of the advantages of this approach increase scalability, better performance, less reliance on other applications, and better overall utilization of resources. However, many IT managers believe that the virtualization of applications provide by public cloud providers is still at an early stage, with many obstacles to making this type of deployment feasible. They also point out that the security demands of hybrid clouds, which include both public and private servers, continue to increase.
Companies that wish to take advantage of cloud computing have vigilant about two things: protecting data from malicious hackers and ensuring that their internal networks do not attack from abroad. It is important for organizations to realize that the best way to fight back against external threats is to build a strong firewall within their own internal networks. Moreover, they should ensure that they are constantly monitoring the health of their public cloud infrastructure and patching any identified holes whenever possible. Companies should also regularly review their security policies to find ways to strengthen them against new attacks. Lastly, they should implement policies that address issues such as identifying malicious behavior, distributing threat information to the FBI, Department of Homeland Security, the U.S. Attorney General, the Federal Bureau of Investigation, and other law enforcement agencies, among others.